In the fast-paced modern and digital world, traditional methods of identity verification such as providing PINs or passwords have become outdated. A truly secured password must be at least 12 characters containing numbers, special numbers, and upper case, or lower case alphabets to prevent it from being replicated or spoofed. Studies indicate that nearly 80% of the individuals use same passwords for multiple accounts, highlighting how effortless it has become to get access to others’ digital accounts. Replacing passwords with accurate ID verification such as passwordless authentication or biometric-based authentication can effectively preserve the integrity of personal data.
What is Passwordless Authentication- A Brief Overview
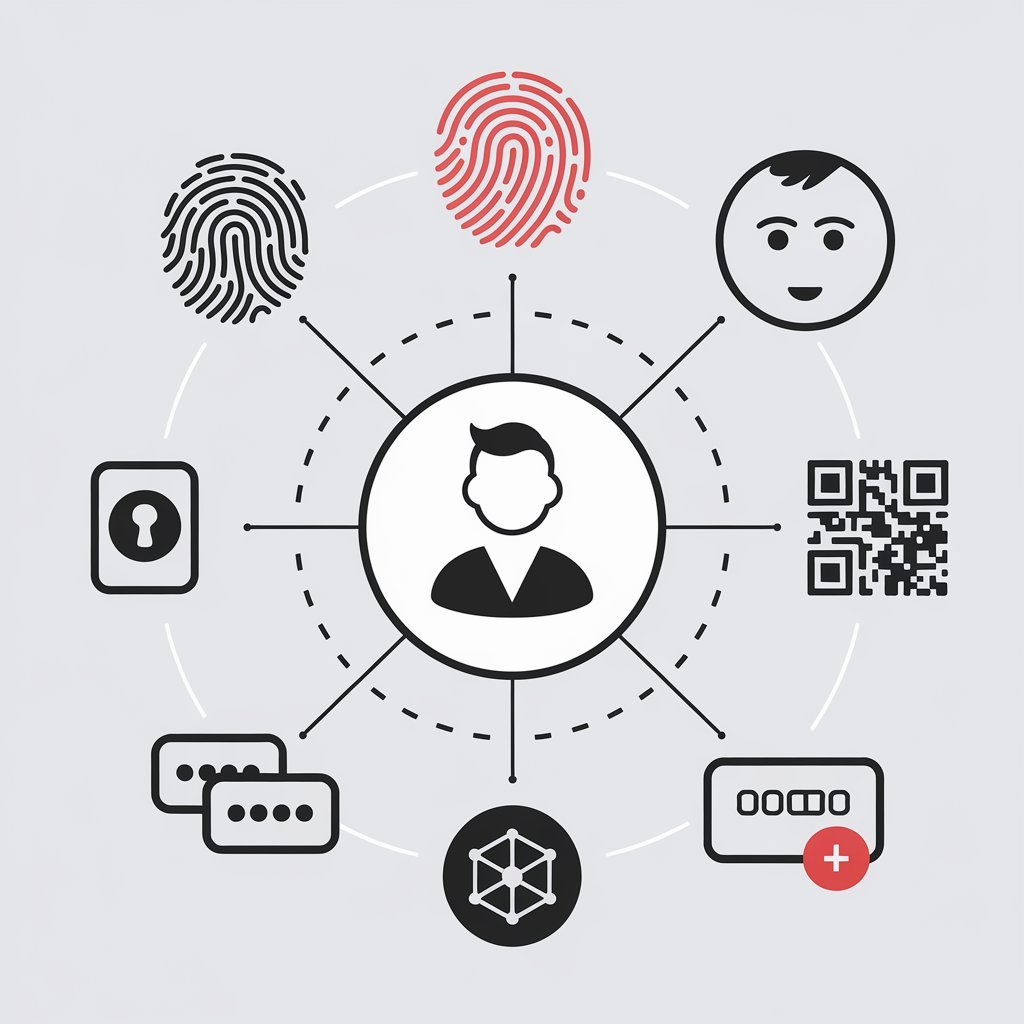
Passwordless authentication is considered a secure and reliable method of ID verification where users are no longer required to remember or provide a complex password and verify their identities either through biometric scanning, OTPs, push notifications, or magic links. The term might sound complicated but it’s way more simpler than remembering long and complex passwords.
Passwordless authentication methods offer enhanced security and reduced costs of maintaining passwords which is an arduous job for businesses.
- Biometric Authentication: It refers to the most accurate type of ID verification where users are authenticated based on their unique biological traits including fingerprints, facial features, or voice patterns. Biological characteristics are challenging to spoof or replicate, providing an accurate and effective alternative to passwords.
- One-time Password (OTP): You might have received OTP while logging into your digital accounts which is effective for one-time use. It eliminates the need to remember complicated passwords and facilitates businesses in reducing the cost required to maintain passwords.
- Push Notifications: It is deemed as the ultimate and secure way of authentication where users receive code on their registered devices to get themselves verified. Push notifications add extra layers of security to digital accounts and ensure that specific devices are in users’ possession, thus improving user experience.
- Magic Links: This authentication method is employed in diverse ways including passwordless authentication, friendly login attempts, or account recovery, enhancing security and improving user experience. It refers to providing an email address to get the one-time password to actively log into digital accounts.
3 Essential Approaches to Passwordless Authentication
To secure your digital accounts and preserve the integrity of sensitive information, don’t overshare your data with others. There are some crucial factors that only users can get to know and can accurately authenticate themselves to attain access to services & networks.
- Things Users know
This approach refers to knowledge-based factors or information that only users know such as passwords, answers to specific questions, or PINs. Users may verify their identity just by answering specific questions rather than providing passwords. However, this approach is prone to spoofing or phishing, as users often share their information without knowing the consequences.
- Things Users Have
It refers to possession-based factors including physical tokens, authentication-based apps under users’ possession, or card readers, adding an extra layer of security to ID verification. Users may present these factors to actively authenticate themselves and gain access to services or privileges.
- Things Users are
This method refers to inherence-based factors that are biologically present in every human being and distinct to every person. Unique biological characteristics like fingerprints, facial features, and voice patterns are employed to verify the identity of individuals, warding off fake identities. This is deemed the most accurate ID verification method, as it’s daunting to spoof or replicate biometric modalities.
Benefits of Implementing Passwordless Authentication Methods
Passwordless authentication methods are widely adopted and present benefits to both users and organizations. It makes it effortless for users to gain legitimate access to services or privileges and facilitates organizations to reduce the costs of maintaining passwords for each individual.
Enhanced Security
Passwords are prone to hacking or replication, they are no longer considered a secure way of verifying the identity of users, as cybercriminals have found multiple ways to get their hands on such credentials. No passwords means no illegitimate access to systems. Passwordless authentication methods offer seamless security to digital accounts, as no unauthorized individuals get access to systems and networks.
Improved User Experience
Studies reveal that every individual needs to remember almost 100 passwords for their multiple social media accounts, or sites, taking nearly 12.6 minutes every week to maintain the passwords. Facial authentication or magic links facilitate users by eliminating the need to remember long and complex passwords, thus enhancing user experience. Additionally, it saves time for users who spend a lot of time maintaining and remembering passwords.
Reduced Maintenance Costs
You must not be aware but maintaining and restoring passwords for each individual requires organizations to employ a large workforce and associated support costs. Recovering or maintaining unlimited passwords is also a tiresome task. Passwordless authentication methods significantly reduce support costs and save time.
Last Word
Undoubtedly, passwordless authentication has efficiently replaced traditional methods of ID verification, but, users feel hesitant in adopting new technologies due to unfamiliarity. Additionally, users are concerned about the security and privacy of their sensitive information, which could be effectively resolved by properly communicating and encouraging user acceptance to enhance adaptability.